39 Concept & Architecture #
SUSE Telco Cloud is a platform designed for hosting modern, cloud native, Telco applications at scale from core to edge.
This page explains the architecture and components used in SUSE Telco Cloud.
39.1 SUSE Telco Cloud Architecture #
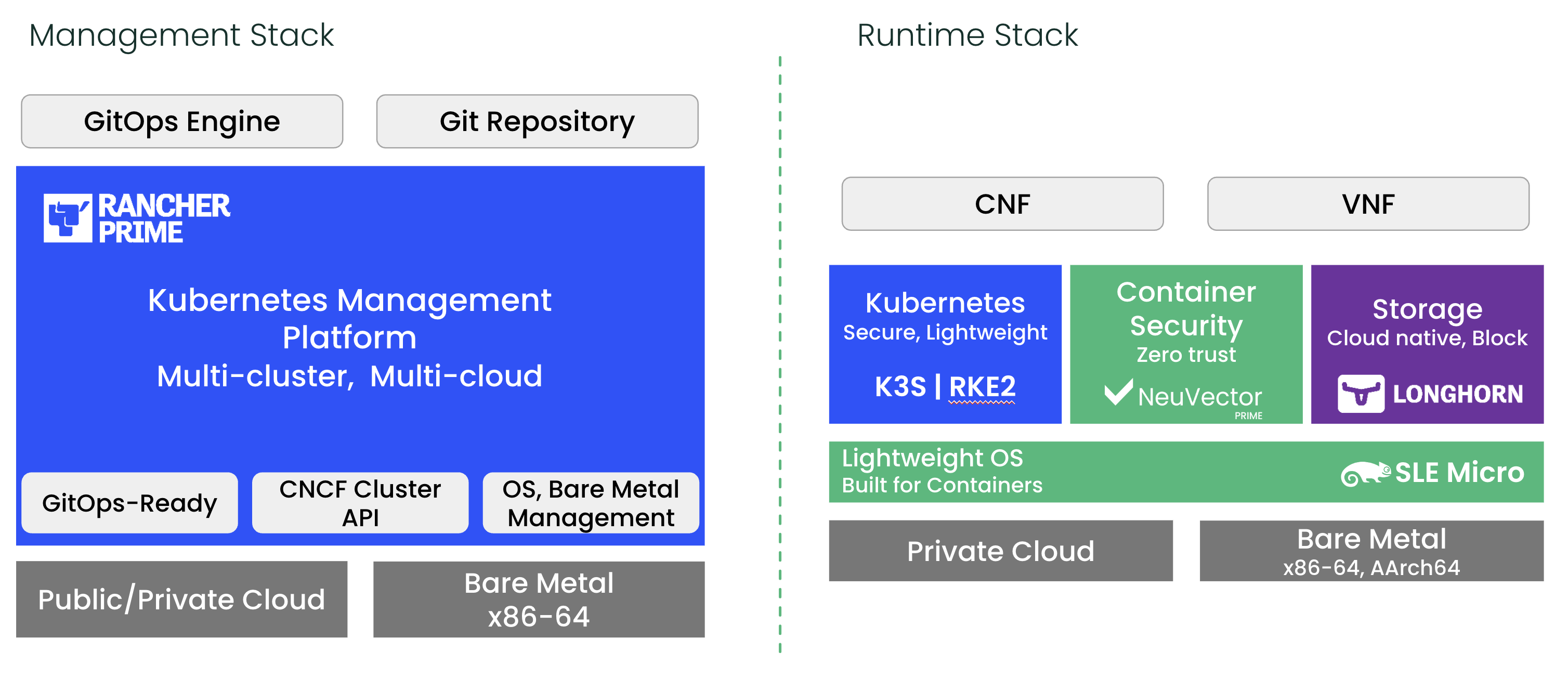
The following diagram shows the high-level architecture of SUSE Telco Cloud:
39.2 Components #
There are two different blocks, the management stack and the runtime stack:
Management stack: This is the part of SUSE Telco Cloud that is used to manage the provision and lifecycle of the runtime stacks. It includes the following components:
Multi-cluster management in public and private cloud environments with Rancher (Chapter 5, Rancher)
Bare-metal support with Metal3 (Chapter 10, Metal3), MetalLB (Chapter 18, MetalLB) and
CAPI(Cluster API) infrastructure providersComprehensive tenant isolation and
IDP(Identity Provider) integrationsLarge marketplace of third-party integrations and extensions
Vendor-neutral API and rich ecosystem of providers
Control the SUSE Linux Micro transactional updates
GitOps Engine for managing the lifecycle of the clusters using Git repositories with Fleet (Chapter 8, Fleet)
Runtime stack: This is the part of SUSE Telco Cloud that is used to run the workloads.
RKE2 (Chapter 15, RKE2) serves as the security-hardened, lightweight Kubernetes distribution, optimized for edge and compliance-focused telecom environments.
SUSE Security (Chapter 17, SUSE Security) to enable security features like image vulnerability scanning, deep packet inspection and automatic intra-cluster traffic control.
Block Storage with SUSE Storage (Chapter 16, SUSE Storage) to enable a simple and easy way to use a cloud native storage solution.
Optimized Operating System with SUSE Linux Micro (Chapter 9, SUSE Linux Micro) to enable a secure, lightweight and immutable (transactional file system) OS for running containers. SUSE Linux Micro is available on AArch64 and AMD64/Intel 64 architectures, and it also supports
Real-Time Kernelfor Telco and edge use cases.
39.3 Example deployment flows #
The following are high-level examples of workflows to understand the relationship between the management and the runtime components.
Directed network provisioning is the workflow that enables the deployment of a new downstream cluster with all the components preconfigured and ready to run workloads with no manual intervention.
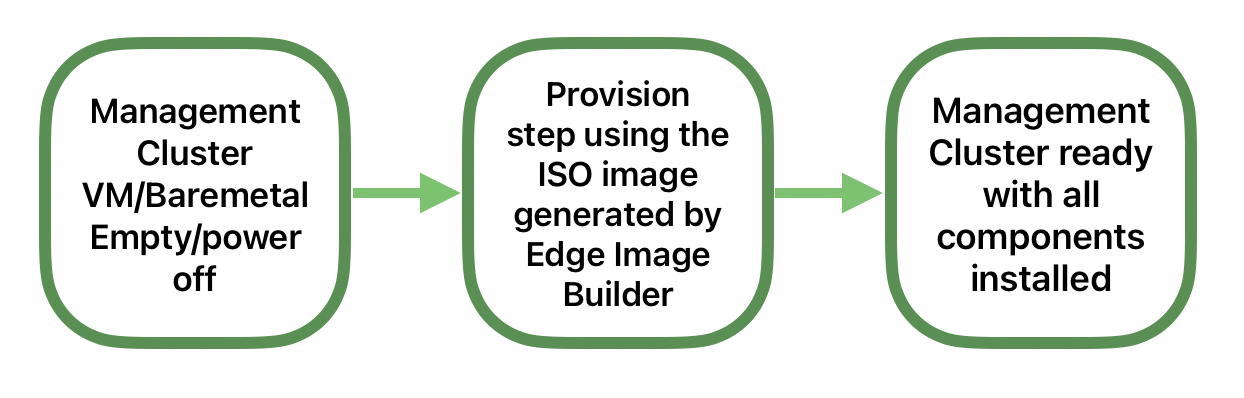
39.3.1 Example 1: Deploying a new management cluster with all components installed #
Using the Edge Image Builder (Chapter 11, Edge Image Builder) to create a new ISO image with the management stack included. You can then use this ISO image to install a new management cluster on VMs or bare-metal.
For more information about how to deploy a new management cluster, see the SUSE Telco Cloud Management Cluster guide (Chapter 41, Setting up the management cluster).
For more information about how to use the Edge Image Builder, see the Edge Image Builder guide (Chapter 3, Standalone clusters with Edge Image Builder).
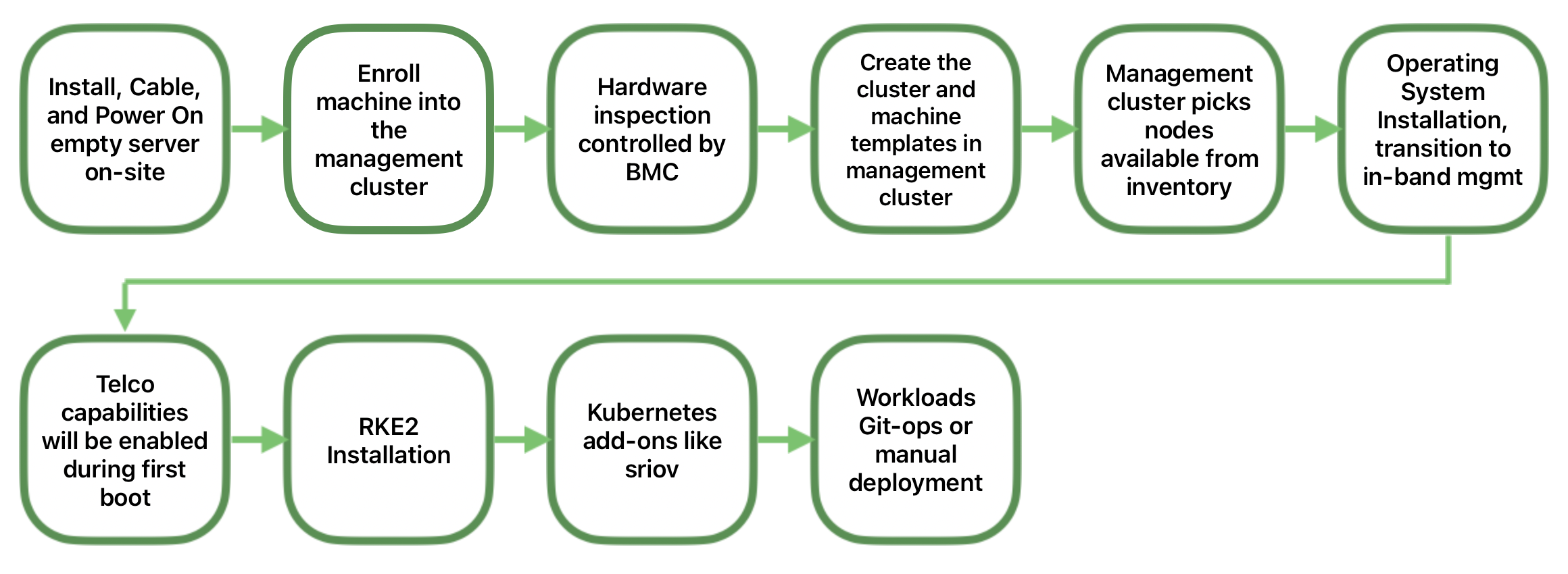
39.3.2 Example 2: Deploying a single-node downstream cluster with Telco profiles to enable it to run Telco workloads #
Once we have the management cluster up and running, we can use it to deploy a single-node downstream cluster with all Telco capabilities enabled and configured using the directed network provisioning workflow.
The following diagram shows the high-level workflow to deploy it:
For more information about how to deploy a downstream cluster, see the SUSE Telco Cloud Automated Provisioning guide. (Chapter 43, Fully automated directed network provisioning)
For more information about Telco features, see the SUSE Telco Cloud Telco Features guide. (Chapter 42, Telco features configuration)
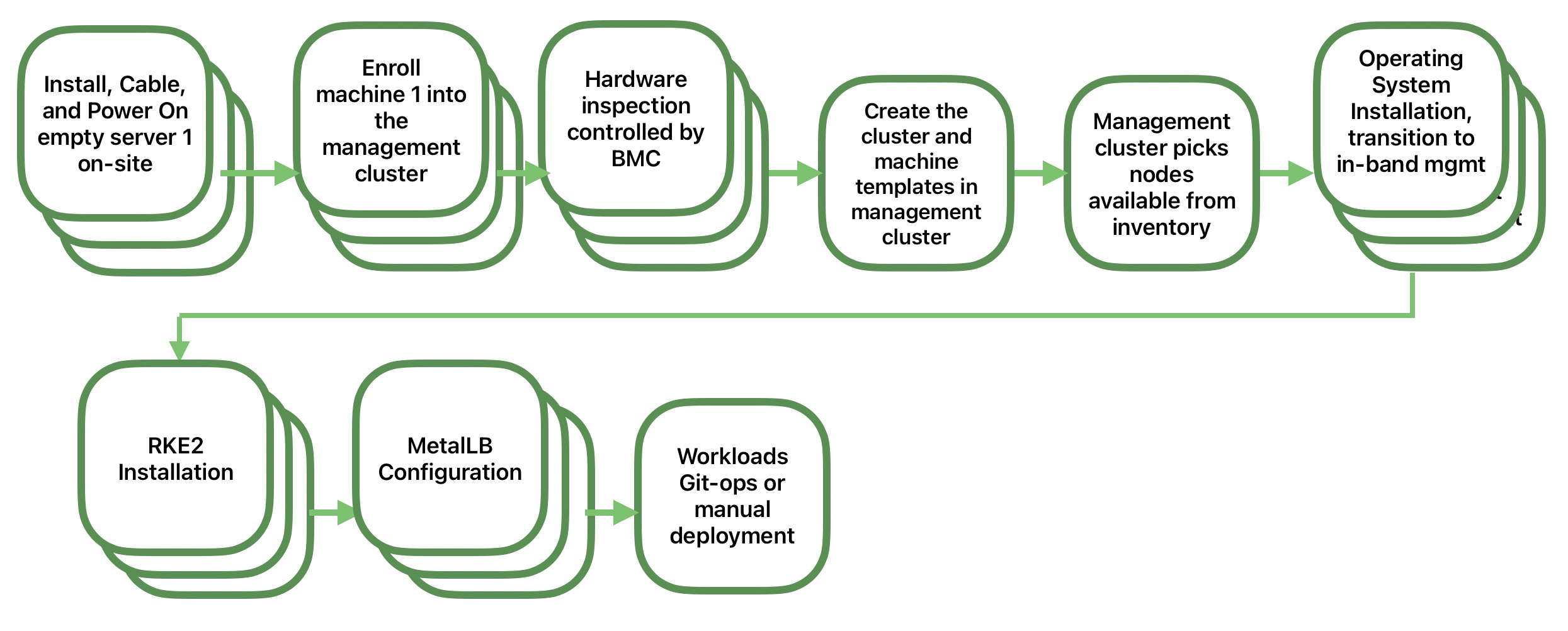
39.3.3 Example 3: Deploying a high availability downstream cluster using MetalLB as a Load Balancer #
Once we have the management cluster up and running, we can use it to deploy a high availability downstream cluster with MetalLB as a load balancer using the directed network provisioning workflow.
The following diagram shows the high-level workflow to deploy it:
For more information about how to deploy a downstream cluster, see the SUSE Telco Cloud Automated Provisioning guide. (Chapter 43, Fully automated directed network provisioning)